The evolution of blockchain technology depends on the resolution of several factors that currently limit blockchain technology, such as speed and scalability.
Internet Computer holds the key to unlock the door that will enable the third revolution of blockchain technology, and it is called "Chain Key Technology."
Consensus on Bitcoin and Ethereum
As the first blockchain, Bitcoin targets the Proof-of-Work (PoW) consensus mechanism that requires miners to solve complex cryptographic mathematical puzzles to get rewarded with a certain amount of Bitcoin. Its main weakness is its lack of speed, with transactions typically taking 30-60 minutes to complete.
Ethereum, which was developed a few years later, used an updated form of Proof-of-Work to speed things up, but it is still far from achieving the web speed needed to deliver compelling online user experiences. The Proof-of-Stake (PoS) consensus model is part of the developer community's strategy to scale Ethereum via the Ethereum 2.0 upgrades.
In this model, miners validate transactions based on how many coins they hold. However, as noted in the Ethereum Developer Resources, “Getting PoS right is a big technical challenge and not as straightforward as using PoW to reach consensus across the network.”
Consensus on the Internet Computer
Internet Computer uses Threshold Relay consensus, which is heavily optimized through the Proof-of-Stake (PoS) model. It emphasizes transaction finality by implementing a Threshold Relay technique in conjunction with the BLS signature scheme and a notarization method to address many problems associated with PoS consensus.
In the Internet Computer version, nodes produce a random number, called a “random beacon,” which is used to select the next group of nodes and drive the platform’s protocols.
Chain Key Technology - a 48-byte Public key
Chain Key cryptography is one of the fundamental breakthroughs enabling the Internet Computer to scale to millions of nodes. It is a set of cryptographic protocols that orchestrate the nodes that make up the Internet Computer and the engine that drives it and makes its operation possible.
It allows for:
• A single public key. This is a huge advantage for the Internet Computer, as it allows any device, including smart watches and mobile phones, to verify the authenticity of artifacts from the Internet Computer.
• Adding new nodes to form new subnets to scale the network infinitely.
• Replacing faulty or crashed nodes with new ones without ever stopping.
• Reviving subnets even if too many nodes within have failed.
• Upgrading the Internet Computer Protocol seamlessly, allowing the network to fix bugs and add new features.
In addition, the Chain Key Technology is a 48-byte public chain key that renders old blocks unnecessary, which enables the Internet Computer to operate at web speed.
This public key is sufficient for the validation of responses and the computation of the Internet Computer. Consequently, this technology divides the execution of smart contract functions into two types:
- Update calls: finalize transactions that update smart contract state in 1–2 seconds.
- Query calls: any changes they make to state (in this case, the memory pages of canisters) are discarded after they run. Essentially, this allows query calls to execute in milliseconds. This is what allows for super-fast transactions.
In stark contrast, to validate an outcome of a smart contract on Ethereum, an open Ethereum client needs to download 400 gigabytes. To make matters worse, the required download size only grows linearly with time: The required size has doubled within a single year; it was only around 200 gigabytes a year ago.
Explore the Technology in this Technical Presentation
Jan Camenisch, who is the Vice President of Research & Crypto at DFINITY, explains Chain Key Cryptography in the following video:
Chain Key Technology by Jan Camenisch
In addition, Manu Drijvers, a cryptography researcher at DFINITY, talks with Arthur Falls about Chain Key technology, answering many of the questions about the inner workings of the Internet Computer. You can listen to the podcast on his Internet Computer Weekly show:
Meanwhile, the Internet Computer’s Network Nervous System (NNS) manages everything from economics and upgrades to onboarding independent data centers and dedicated node machines.
What does Chain Key technology involve?
The Internet Computer blockchain is created by nodes in data centers located around the world running the Internet Computer Protocol (ICP). These node machines are combined to create subnets.
Subnets host canister smart contracts, which are interoperable compute units uploaded by users and contain both code and state. It is important to note that a subnet can be created by combining nodes from different data centers.
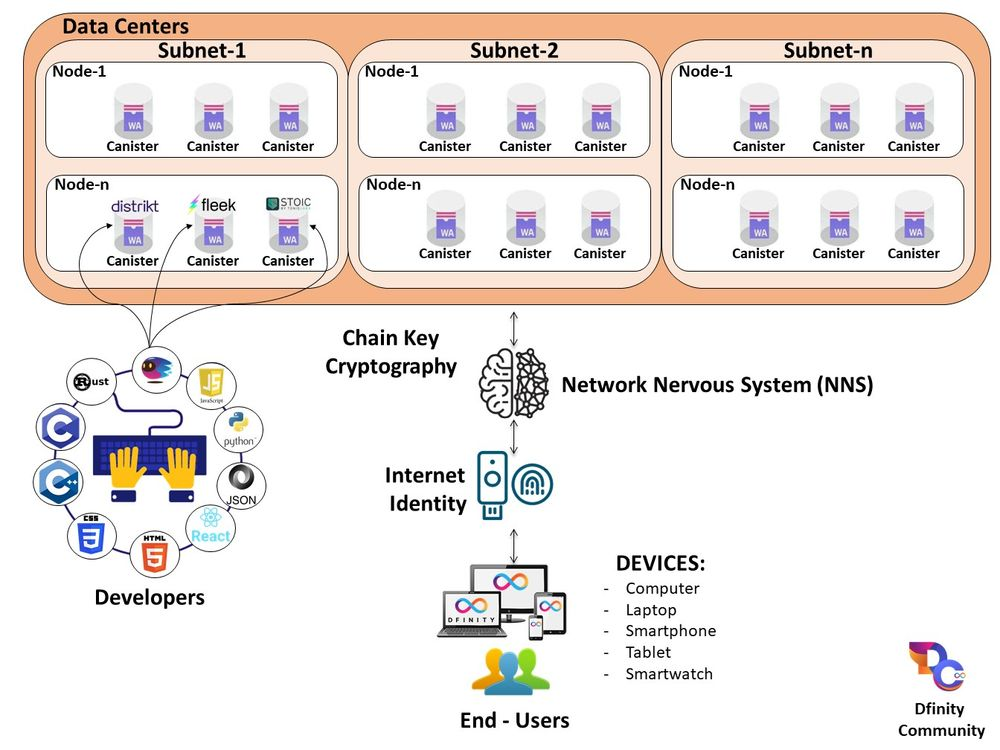
In essence, the Chain Key technology involves the following:
A. NIDKG [ Noninteractive Distributed Key Generation ]
NIDKG is the abbreviation of Noninteractive Distributed Key Generation, an innovative advanced cryptography technology that includes forwarding secrecy and non-interactive zero-knowledge proof encryption.
On Internet computers, the nodes that make up the subnet will change over time, such as introducing old nodes and adding new nodes. By using NIDKG, the subnet can always be referenced by the static public key so that even if the subnet nodes are constantly changing, the key can be managed effectively and securely.
NIDKG/Key Resharing cryptography enabled to bootstrap the network without special ceremonies (e.g., as Z-Cash used). Node machines in the network constantly re-generate their secrets, and the old ones become useless.
Learn more about this topic by watching this video and reading the following article.
B. Single Key for the Internet Computer that certifies a single key per subnet
The most visible innovation of Chain Key cryptography is that the Internet Computer has a single public key. In other words, the blockchain reportedly has a more scalable method of verifying transactions and digital objects than other blockchains have.
The video in the previous section explains the single public key in detail. If you haven't watched it, you can find a summary in the following video.
C. Protocol upgrades
One of the many duties of the NNS is to make upgrades to the Internet Computer Protocol network that the community has voted on. Making upgrades to the blockchain requires the solution of several challenges created by running a decentralized protocol, including allowing arbitrary changes to the Internet Computer protocol, preserving all states, minimizing downtime, and rolling out upgrades autonomously.
The "catch-up packages" (CUPs) allow for upgrading the Internet Computer Protocol itself.
A "catch-up package" (CUP) bundles all the information a node requires to participate in the subnet. It also enables existing nodes to resume operation in cases such as when theywere cut off from the network.
The idea here is to instruct the nodes of a subnet to run a different version of the protocol after the next "catch-up package" has been produced. This makes it possible to fix bugs in the protocol, add new features, and so on. It is probably the most crucial feature that will allow for the Internet Computer to run in perpetuity.
Learn more about this topic by watching this video.
D. Adding and removing nodes
Unlike other blockchain projects, the Internet Computer doesn't want all nodes to store the blockchain forever because this gets very large very quickly if you process many messages. If a new node wants to join the subnet, it will never fully view the blockchain because members have already thrown away the old pieces. However, they can offer a "catch-up package," which can be trusted because the Chain Key signs it. With this CUP, a node can securely jump ahead to a recent point of the blockchain.
In summary, this mechanism makes it easy for a node to catch up to the latest state of a subnet. This allows us to easily add new nodes to a subnet (which may replace faulty/corrupt nodes). Additionally, since the CUP serves as a "checkpoint" of the blockchain, this is a clear cutoff point where we can upgrade the protocol.
E. Resumption & amp; State sync
A subnet is composed of "replica nodes" drawn from data centers that collaborate to replicate data and computations involved with hosted canisters. Replicas create a “catch-up package” every at a certain frequency (e.g., 200 rounds) signed using the subnet key.
Therefore, canisters get security and reliability through replication, enabling nodes on the Internet Computer blockchain to resume and catch up to the latest state of the protocol.
A joining node can request the state from its peer nodes already operating the subnet (via a state-sync protocol). As the replicated state may be vast, the CUP only contains a hash of this state, and the full state can be obtained via this protocol.
Learn more about this topic by watching this video.
F. Extended Consensus orchestrating all of this
Since the Internet Computer runs on a network of nodes in independent data centers located around the world, all subnets must process the same messages in the same order to ensure that they achieve the same state.
To ensure that the nodes powering the subnets can agree on the order of messages to process, the Internet Computer relies on a novel consensus protocol, as described in the Consensus White Paper.
Learn more about this topic by watching this video and reading the following article.
Applications of Chain Key technology
Internet Computer is faster than other blockchains because it doesn't rely on proof of work or stake: its Chain Key technology and subnets don't save previous blocks globally. Below you can see some of the applications that this breakthrough technology will enable:
- Direct integration of Bitcoin, Ethereum, and the Internet Computer without bridges, relays, hubs or private keys. Directly on the Internet computer, a layer 1 blockchain.
- Bitcoin smart contracts.
- X.509 certificate authority.
- Websites, businesses and users do not need to run a node to interact securely.
- Plus a whole lot more.
Obviously also makes it easy to create DEXs for ICP-BTC-ETH
— Dominic Williams ∞ (@dominic_w) July 6, 2021
Chain Key removes need for hubs, oracles, bridges etc. Can integrate direct.
Smart contracts can sign Bitcoin+Ethereum tx without holding private keys (network signs on behalf of contract using Chain Key tech)
Resources
Chain Key Presentation | Inside the Internet Computer
- Chain Key Cryptography - Medium Post
- Achieving Consensus on the Internet Computer - Medium post
- AMA on DFINITY Subreddit (Ask Me Anything), about Chain Key Technology. Friday, May 28, 2021.
Official DFINITY Channels
Website | Twitter | Youtube | Medium | Github | Telegram | Reddit | Facebook | Instagram | LinkedIn | Developer Forum | Discord | The Reboot
Connect With Us:
Twitter | Telegram | Instagram | Facebook | Email

- Disclaimer: The views and opinions expressed on this website are solely those of the original author and other contributors. These views and opinions do not necessarily represent those of the Dfinity Community staff and/or any/all contributors to this site.


Comments are for members only. Join the conversation by subscribing 👇.